Linux OS namespace v/s container, pod and worker node
Namespace:
- mnt (Mount),
- IPC,
- net (Network),
- PID,
- user (user and group)
- and UTS (=Unix Time Sharing. Host name and domain name).
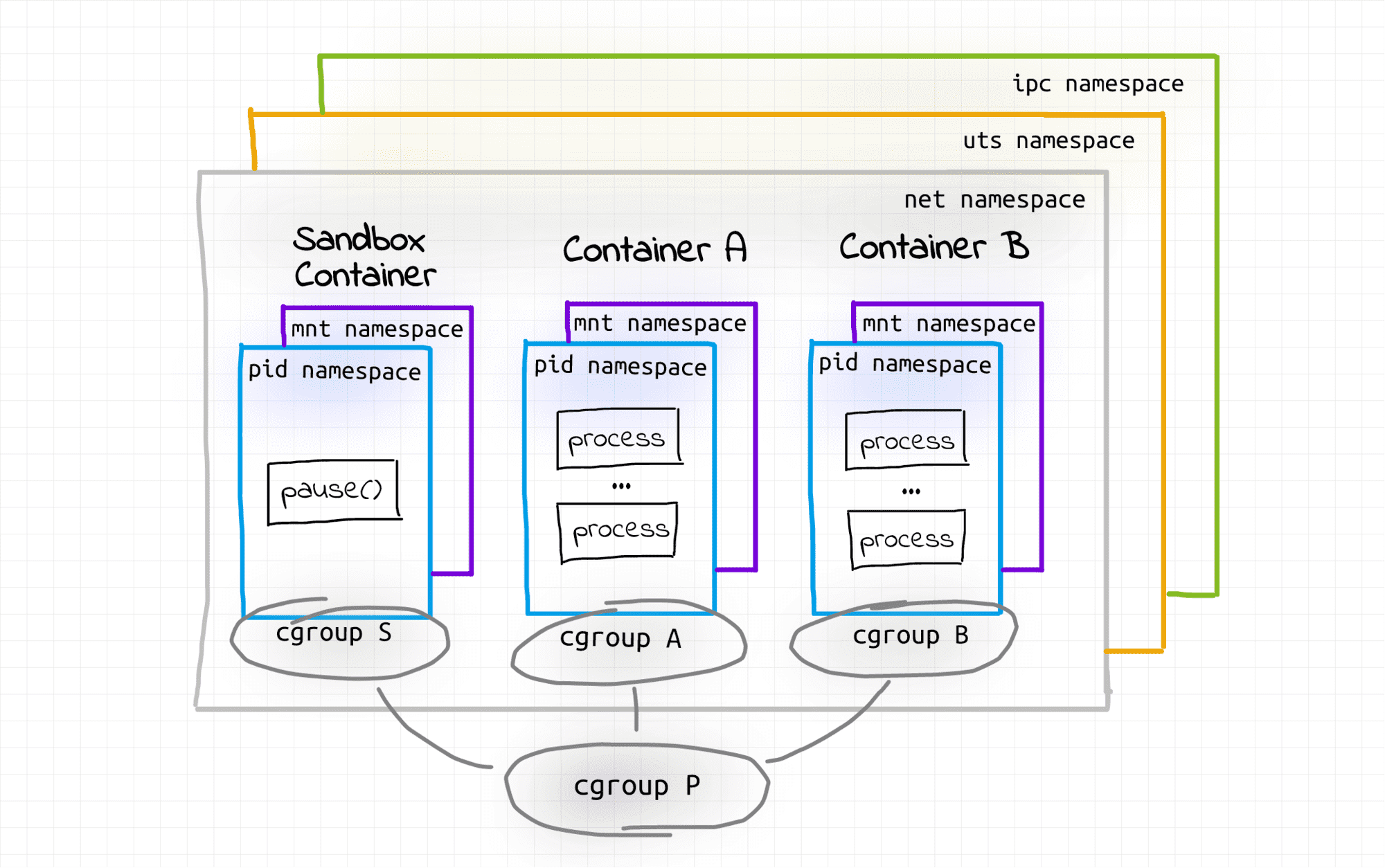
Within pod, each container have its own mnt space.
Within pod, each container may or may not have its own pid namespace, depending on value for shareProcessNamespace flag at pod specification.
Pause container has all 6 namespaces. Other container(s) having only pid and mnt namespace. They share net, uts, user and ipc namespace.
So containers within pod can communicate over
- Localhost IP: 127.0.0.1
- Shared domain name / host name
- IPC: shared memory, message queue etc.
So in terms of namespace and cgroups, pod looks like this:
We can control sharing of namespace among container, sidecar container within pod and worker node with following flags at pod specification.
- shareProcessNamespace
- hostPID
- hostNetwork
- hostIPC
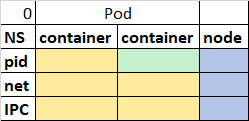
- No. 0 is default case, We do not specify any flag. All four flags are set as false. So inside pod both container have its own pid namespace. Worker node has its own pid, net, ipc namespace.
- No. 1 hostIPC = true. So pod (both container) and worker node share IPC namespace
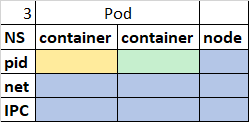
- No. 5 hostPID = true and hostIPC = true. So pod (both container) and worker node share PID namespace and IPC namespace
- No. 6 hostPID = true and hostNet = true. So pod (both container) and worker node share PID namespace and Network namespace
- No. 7 hostPID = true, hostNet = true and hostIPC = true. So pod (both container) and worker node share PID namespace, Network namespace and IPC namespace
- No. 9 shareProcessNamespace = true. So both containers share PID namespace. hostIPC = true. So pod (both container) and worker node share IPC namespace
- No. 10 shareProcessNamespace = true. So both containers share PID namespace. hostNet = true. So pod (both container) and worker node share Network namespace.
- No. 11 shareProcessNamespace = true. So both containers share PID namespace. hostIPC = true. hostNet = true. So pod (both container) and worker node share Network namespace and IPC namespace





















0 comments:
Post a Comment