3. Install : Image Supply Chain
Trow: Registry and image management
Prisma Cloud: Cloud Security Platform
NeuVector: scan container images for vulnerabilities. DPI, Firewall
Clair: static analysis for container image vulnerabilities. Open Source Project
Aqua: Complete enterprise security solution for container LCM
Trivy: scan container images for vulnerabilities.
use command
trivy image "image name" | more
trivy i "image name" | more
They provide all CVEs. Summaries number of CVE: high, medium, low, critical, unknown.
Note, it is "trivy i" it is not "trivy -i"
Trivy can find misconfiguration and vulnerabilities in (1) file system and (2) git repository.
We can check all YAML file with command
trivy conf "folder path of YAML files"
Notary: TUF based CNCF project. Image signing
Harbor: secure registry and manage artifacts
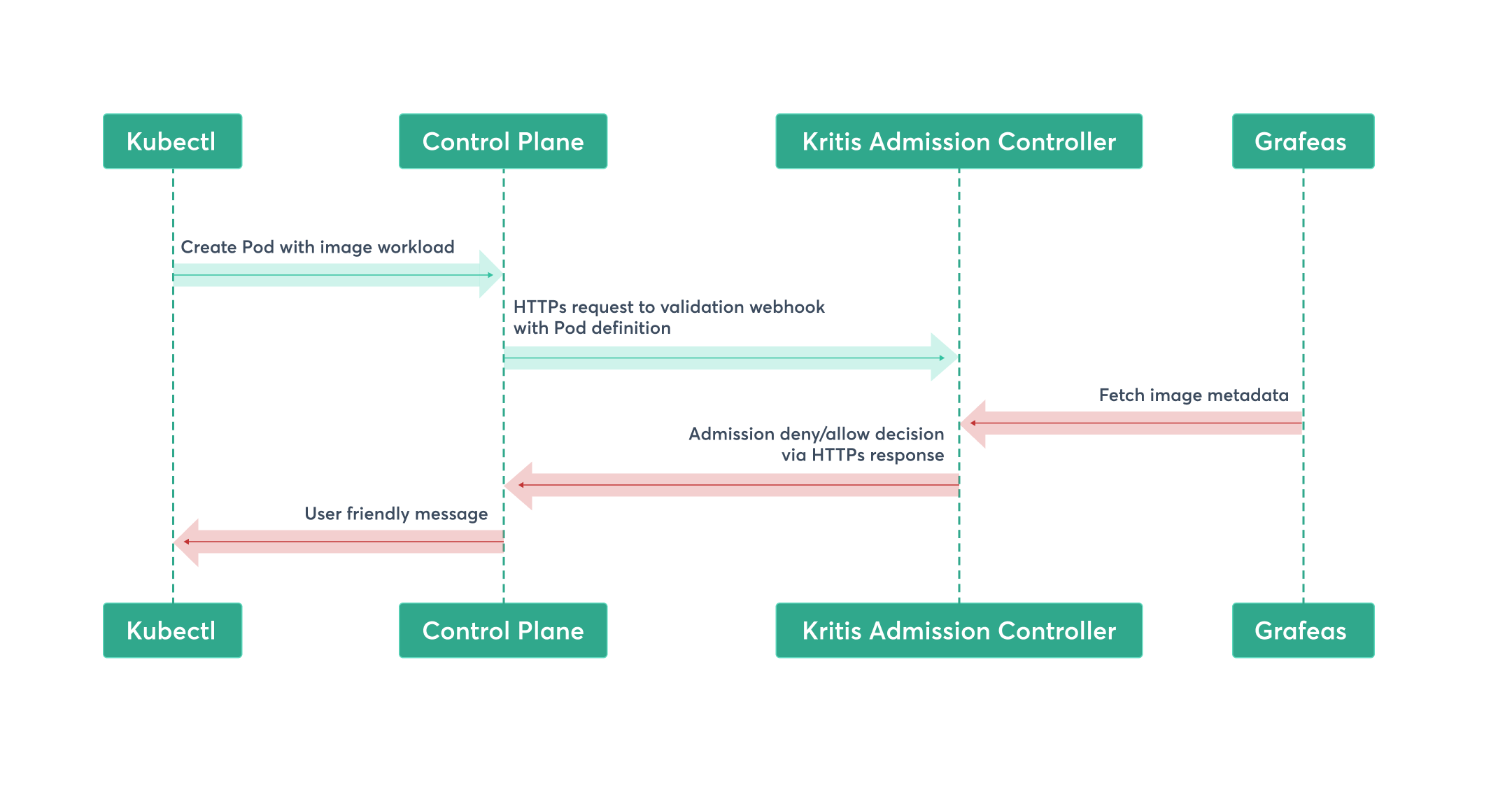
Kritis: Validation webhook of K8s admission controller and CRDs. It uses Grafeas and Voucher.
1. GenericAttestationPolicy : kritis.grafeas.io/v1beata1
spec: attestationAuthoriy
2. AttestationAuthority: kritis.grafeas.io/v1beata1
spec: privateKeySecretName, publicData, noteReference.
3. ImageSecurityPolicy: kritis.grafeas.io/v1beata1
spec: imageWhitelist / imageAllowlist
spec: packageVulnerabilityRequirement
maximumSeverity:
whitelistCVEs: / allowlistCVEs
4. Default admittance fallback policy
Grafeas: API for image vulnerabilities meta data, attestation meta data all other structured metadata for artifacts.
Terminology
Note: High level description of type of metadata. E.g. CVE as Vulnerability Note. Note ID format: /projects/"project_id"/notes/"note_id"Note ID is unique within project. It can be CVE ID
Occurrence: instance of note in artifact E.g. CVE presence in an image. Occurrence ID format: /projects/<project_id>/occurrences/<occurrence_id> Occurrence ID is random number
Providers: E.g. Vulnerability scanning. add notes and occurrence in DB
Consumer: E.g. Kritis
Resource URL: Part of occurrence. It is identifier for artifact. Immutable. It ties occurrence to image
Kind Specific Shema: Strict and structured. ATTESTATION, BUILD, DEPLOYMENT, DISCOVERY, IMAGE, PACKAGE, VULNERABILITY, INTOTO. Total 8. Easy to add new. It helps to support multi-vendor.
The metadata can be part of binary authorization tool.
Architecture
Auth system for strict access control.
Client: not part of Grafeas
Grafeas API: core component
DB: Pluggable storage backends
Voucher: Make sure image after build and image at deployment, both are same.











0 comments:
Post a Comment