Securing Wireless Cellular System
It was started with introduction of ACM (Association for Computing Machinery). The
Arvind started with introduction of his employer. SLOKA started in 2004. Now about 30 people are working with SLOKA. At present SLOKA provides solution for Fixed WiMAX (IEEE 80.16d). They have roadmap for LTE & Mobile WiMAX (IEEE 80.16e) as well.
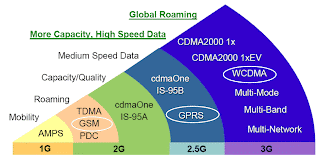
Arvind started with some background of various wireless system, generations, architecture and protocol stacks. This slide I liked that shows various generations of wireless system evolution with both stream 3GPP and 3GPP2.
After this background, we discussed the main topics and he listed out possible security threats, security goals and security context. Generally standards are written more for mobile handset. For network equipment side, many things left open. AKA stands for Authentication & Key Agreement.
We had interesting discussion on challenges to implement number portability. For
He explained security in GSM, with AKA and LAU procedure. The SIM card have A3, A8 and A5 algorithm. A3 and A8 are used for authentication, during LAU and incoming call. A5 is used for encrypting the data/voice, if it is enable. These algorithms are on SIM card. SIM card do not have CPU. It is implemented with hardware logic. They are proprietary algorithms. Standard recommends COMP128 so in early days everyone implemented that only. In 1998, some document got leaked. The biggest flow about this approach is Ki, which never changes. Audience suggested, can we read Ki if we have memory dump of the SIM card. Yes, we can, but the challenge is to identify the Ki in the memory dump. Unlike Ki, Kc frequently changed. Kc is just 54 bits/bytes so comparatively easy to derive, by reverse and A8. Yes for A3 and A8, ECC is best algorithm, theoretically but difficult to implement in SIM card. Nowadays COMP128-2 and COMP128-3 are used. TMSI allocation and AKA both are independent procedure, but may happen together, generally at the time of LAU.
He listed these three approaches to identify Kc, and crack encryption algoritham.
1. Compare known palin text with encrypted text
2. Differntial analysis of 2 sets of plain texts and encrypted texts
3. Side channels IBM standard with RF monitoring.
Here is the presentation file:
Next discussion about security aspects for 3G UMTS network, and how it is different from GSM. Here we have two way authentication. Even UE also authenticate network. So in stead of authentication triplet now we have authentication quintet. He explained RRC security procedure. We have also START, THRESHOLD and counter check mechanism to prevent man in the middle attack. It uses for session lifetime. At UMTS 3G network, we have CK for encryption (Kc in GSM) and additional key IK for integrity of the data. GSM uses CKSN, while UMTS uses KS1 from SIM card. In UMTS the data flow is suspended and resumed before changing key. There are various inputs to f8 algorithms like Ck, count-C, Bearer direction. Output is keystrem block. FRESH, direction, counter-1, message and IK are input for f9 algorithm to generate MAX-1. Here message is Radio bearer ID, RRC Sequence number and signaling content. USIM and AuC are involved. CK, IK, XRES, MACA-A etc used. UMTS has Radio Bearer, that is similar to service flow in WiMax. Two types of Radio bearers Data and Signaling.
Someone from audience shared and innovative way to fraud with mobile operator, that they used to do during college days. If we make a call, talked it and then do not disconnect, but remove the battery. So bill do not get generated. When we remove the battery, the necessary signaling information do not exchange to terminate the call. So it was bug in billing system. Other person confirmed that yes sometimes operators choose low quality billing solution. We mentioned the mobile operator and its billing solution provider name also, that I prefer not to disclose at my blog. :)
Yes, Arvind added that multiparties are involved to secure the network. And the operator has to take care of possible security threat from contractor. He added that VISA wanted to implement some online transaction solution in SIM card. So your SIM card (so your mobile) act as credit/debit card. However, VISA and mobile operators both parties were not comfortable to share some secret details about security implementation. In the field of security, the publicly published algorithms are more secured. As all have tried to crack it and so made it more robust.
Arvind discussed some interesting scenarios for UMTS about backward compatibility with GSM. Our mobile handset, our SIM card and the network, all the three elements can be either 2G GSM or 3G UMTS. 2G GSM system uses KC, while UMTS sues CK and IK both. 3G UMTS SIM card is USIM, 2G mobile is MS and 3G mobile is UE. conversion is standard algorithm. The attachment is between USIM and AuC. If USIM with 2G MS joined to 2G GSM network. USIM has CK, IK that should be converted to KC and XRES to SRES. This implementation is at USIM, so not standardized. But if USIM with UE joined to GSM network then conversion happened at UE. It is from CK+IK to KC, so need to standardized.
At last, Arivind gave some algorithmic background, like ciphering type, data integrity and encryption some basic popular algorithm. Fro UMTS 3G, the f8 and f9 algorithams are based on KASUMI. KASUMI means mist in Japanese. It is block cipher. MISTY algorithm for block cipher, by Mitsubashi, is in public domain. And as name suggest, KASUMI is based on MISTY. A5, A3, GRE3 algorithams are based on KASUMI. One can always have two choices, to implement these algorithm. Hardware and software. For network side, it does not matter much. However for mobile handset side, this choice has much impact. The software implementation we can always optimize and fine tune as per underlying hardware. Yes, in one of the project, I further optimized Diffie-Hellman key exchange algorithm for 32 bits and 64 bits processor.
We discussed about end-to-end security. Even today, also our landline phones are not secure. Anyone, can tap the line and listen the conversation. Yes, we can find some device to encrypt/decrypt voice with Internet help. Since it is proprietary solution, both party has to use these product. For GSM in
We talked about 3G, since BSNL had recently launched it. generally 3G phones are high end phone. However in the like
Overall it was very good session. Arvind involved the audience in the talk and handled the question-answers very nicely. Even some were less relevant questions. I met some of my ex-colleagues from Lucent (now Alcatel-Lucent). I am thankful to the speaker Arvind, ACM and my friend Jayesh, who informed about this session on chatting.
Here, it is my humble effort to share my notes, as what I remember. Many points are not verbatim. Please correct me, add/modify this content, if you have also attended this session. One can also refer Arvind's blog to know more about this session. If you like this article, then you may also like to read about my other such notes on :1. Sensor Netwroks
2. WCDMA/HSDPA
3. WiMAX
4. www.bdotnet.in Launch!









4 comments:
Very good article :-)
Keep it up... :-)
That was huge post. Pretty interesting.
Cheers Mate
One can get all PPT from 6th ETSI Security workshop. Click here:
http://docbox.etsi.org/Workshop/2011/201101_SECURITYWORKSHOP/
Also some interesting PPT here
http://www.slideshare.net/zahidtg
An interesting article about virtual SIM
http://www.nfcworld.com/2011/11/09/311213/apple-patents-sim-within-secure-element-technology/
Post a Comment